
In today’s world, where work happens everywhere and cyber threats lurk around every corner, traditional network security is showing its age. Enter the Zero Trust approach, powered by technologies like SASE, CASB, and DLP. But what exactly are these things, and why should your business care? Let’s break it down in plain English.
The Old Way: Castle-and-Moat Network Security Explained
Traditionally, businesses set up their networks like medieval castles:
- A strong perimeter (firewall) guards the entrance
- Once inside, you’re mostly trusted to roam freely
- Most security resources focus on protecting the border
- Remote access requires poking holes in your defenses (VPNs)
This is what security pros call a “hub-and-spoke” model. Your main office or data center is the hub, and connections to branch offices, remote workers, and the cloud are the spokes.
Think of it like a gated community with a security guard at the entrance. Once you’re past the gate, nobody questions whether you belong in any particular house.
Why Traditional Network Security Fails in a Cloud and Remote Work Era
This approach made sense when:
- Most work happened in the office
- Most applications lived on servers you owned
- Threats mainly came from outside your network
But today:
- Work happens everywhere—home, coffee shops, airports
- Applications live in the cloud
- Devices connect directly to the internet
- Hackers target people, not just networks
The castle walls have effectively disappeared. When your “inside” and “outside” blur together, the old approach falls apart.
The New Way: Zero Trust Security with SASE, CASB, & DLP

Zero Trust flips the old model on its head with one simple principle: never trust, always verify.
Instead of assuming everyone inside your network is trustworthy, Zero Trust checks every single access request, no matter who makes it or where it comes from.
What is Secure Access Service Edge (SASE)?
SASE (Secure Access Service Edge, pronounced “sassy”) is like a security checkpoint in the cloud that follows your users everywhere.
Imagine if, instead of having guards only at your building entrance, every employee carried a personal security guard who:
- Checks their ID constantly
- Inspects everything they touch
- Only lets them enter rooms they’re authorized to access
- Monitors for suspicious behavior
That’s SASE—it combines networking and security into a cloud service that protects access no matter where your people, applications, or data live.
What is Cloud Access Security Broker (CASB)?
CASB (Cloud Access Security Broker, pronounced Caz-bee) is like having a specialized security detail just for your cloud applications.
Think of it as a security middleman that sits between your users and cloud services (like Office 365, Salesforce, Dropbox, or other SaaS applications) and:
- Monitors who’s using what
- Spots unusual activity
- Prevents sensitive data from leaking
- Enforces your security policies consistently
If SASE is your general security force, CASB is your specialized cloud security team.
What is Data Loss Prevention (DLP)?
DLP (Data Loss Prevention) is like having security guards specifically watching over your sensitive information. These guards make sure your important data doesn’t leave the building without proper authorization.
Think of DLP as:
- Security officers who inspect every document, email, and file
- Guards who recognize what information is confidential
- Specialists who can spot when someone is trying to take sensitive data where it shouldn’t go
- A system that can automatically stop data from leaking, whether accidentally or deliberately
In a Zero Trust environment, DLP becomes even more powerful because it’s integrated with other security components. Instead of just watching exit points, it can monitor and protect data everywhere it exists—on devices, in transit, and in cloud applications.
How Zero Trust, SASE, CASB, and DLP Work Together to Secure Access
Let’s see how this plays out in real life:
Scenario: An employee accessing company data
In the old hub-and-spoke model:
1. Employee connects to the company VPN
2. Once connected, they can access many internal resources
3. Security checks happen mainly at the VPN entry point
4. Potential attackers who get past this point gain broad access. This is known as “lateral movement”.
In a Zero Trust model with SASE/CASB:
1. Employee attempts to access a company application
2. The SASE service verifies:
• Who they are (Identity)
• What device they’re using
• Whether the device is secure
• Their location and time of access
• If their behavior matches normal patterns
3. Based on all these factors, access is either granted, limited. or denied
4. CASB adds extra checks for cloud applications:
• Is the user allowed to access this data?
• Are they trying to download sensitive information?
• Are they accessing from an approved application?
5. DLP constantly monitors data movement:
• Is someone trying to download financial records to a personal device
• Is an employee emailing customer data outside the company?
• Is sensitive information being copied to unauthorized cloud storage?
• Is there unusual movement of large amounts of data?
6. All traffic is inspected, regardless of location
7. Every access request is evaluated independently
The key difference? In Zero Trust, there’s no concept of being “inside the network” and gaining broad access. Every single request is evaluated on its own merits.
Visual Comparison: Hub-and-Spoke vs. Zero Trust SASE
Traditional Hub-and-Spoke:
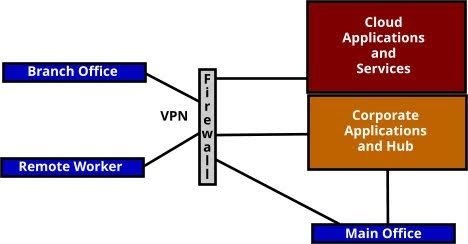
- All traffic routes through central location
- Security checks mainly at perimeter
- VPNs required for remote access
- Limited visibility into cloud usage
Zero Trust with SASE:
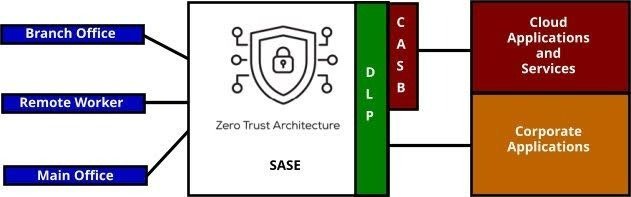
Security follows the user, not the network
- Direct, secure access to any resource
- Consistent policy enforcement everywhere
- Full visibility across all connections
Top Benefits of Zero Trust Security for Remote Work and Cloud Applications
1. Better Security
- Limiting damage from breaches (no lateral movement)
- Reducing your attack surface
- Protecting remote work without compromising security
- Consistent protection for cloud applications
- Preventing sensitive data leakage through comprehensive DLP
- Maintaining control of critical information across all channels
2. Better User Experience
- No more clunky VPNs
- Direct access to resources from anywhere
- Faster connections (no routing through headquarters)
- Seamless security that follows users
3. Better Control
- Single set of policies applied everywhere
- Complete visibility into all access and data
- Easier compliance with regulations
- Adaptable to changing business needs
Looking to reduce risk and protect your organization? Explore our cybersecurity services to learn how we help businesses implement Zero Trust, endpoint protection, and data loss prevention strategies.
How to Implement Zero Trust: A Practical Step-by-Step Guide
Implementing Zero Trust with SASE and CASB doesn’t happen overnight. Here’s a practical approach:
Step 1: Know Your Assets
Inventory your applications, data, and users. What needs protection? Who needs access?
Step 2: Focus on Identity First
Strong authentication is the foundation. Implement:
- Multi-factor authentication
- Single sign-on
- Risk-based access policies
Step 3: Start with High-Value Targets
Begin protecting your most sensitive applications and data first. Implement DLP controls for your most critical information.
Step 4: Implement in Phases
- Phase 1: Monitor mode to understand normal patterns
- Phase 2: Apply policies to specific user groups
- Phase 3: Expand coverage across your organization
Step 5: Partner Wisely
Choose vendors that offer integrated SASE, CASB, and DLP capabilities that match your needs or partner with a cybersecurity-focused managed IT provider—whether you need fully managed support or a co-managed IT solution that works alongside your internal team.
Real Company Example
Consider a 200-person financial services firm that switched to Zero Trust with SASE/CASB:
Before:
- All remote workers used VPN to access company resources
- Cloud application usage wasn’t fully monitored
- Security team had limited visibility into user activity
- Data loss prevention was inconsistent or nonexistent
- Sensitive data could easily be downloaded to personal devices
After:
- Employees access applications directly, no VPN needed
- All access is verified based on user, device, and context
- Sensitive financial data is protected consistently everywhere
- DLP policies automatically prevent data exfiltration attempts
- The system can detect and block unusual data transfers in real-time
- Security alerts dropped by 60% (fewer false positives)
- IT gained visibility into previously “shadow IT” applications
Why Zero Trust Security Is the Future of Cyber Defense
The shift to Zero Trust with SASE, CASB, and DLP isn’t just a technology change – it’s a mindset shift. Instead of building bigger walls, we’re creating smarter security that focuses on what matters: protecting people, data, and applications wherever they are.
For businesses facing today’s realities of remote work, cloud adoption, and sophisticated threats, this approach offers a practical path forward that improves both security and user experience while ensuring sensitive data remains protected at all times.
The days of the castle-and-moat are over. In a world where work happens everywhere, security must follow suit.
Is your organization considering Zero Trust? What challenges do you face in moving beyond traditional network security? Let us know how we can help.
About KML Computer Services
KML Computer Services is a trusted managed IT provider based in Michigan and South Carolina, serving businesses locally and across the U.S. We help organizations strengthen their security with modern solutions like Zero Trust, SASE, and DLP—backed by hands-on support and deep industry expertise.
Contact us to learn how we can help secure your systems and support your team.
Sidney Rossi with over 25 years of software sales, including hardware and software, is not only seen as a leader in the technology industry, but a proven performer.

